FireEye
 FireEye has invented a purpose-built, virtual machine-based security platform that provides real-time threat protection to enterprises and governments worldwide against the next generation of cyber attacks. These highly sophisticated cyber attacks easily circumvent traditional signature-based defenses, such as next-generation firewalls, IPS, anti-virus, and gateways.
FireEye has invented a purpose-built, virtual machine-based security platform that provides real-time threat protection to enterprises and governments worldwide against the next generation of cyber attacks. These highly sophisticated cyber attacks easily circumvent traditional signature-based defenses, such as next-generation firewalls, IPS, anti-virus, and gateways.
The FireEye Threat Prevention Platform provides real-time, dynamic threat protection without the use of signatures to protect an organization across the primary threat vectors and across the different stages of an attack life cycle. The core of the FireEye platform is a virtual execution engine, complemented by dynamic threat intelligence, to identify and block cyber attacks in real time.
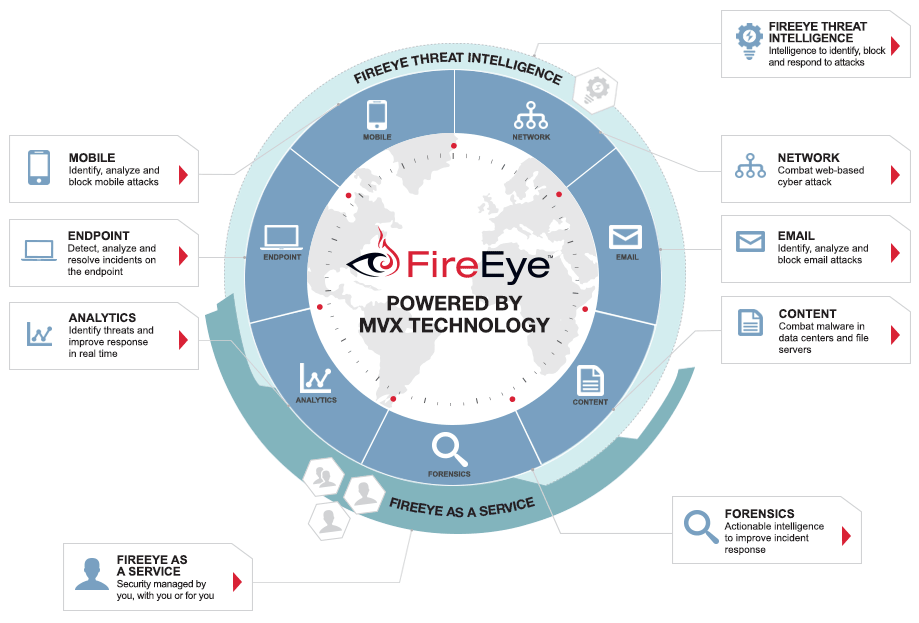
Advanced cyber attacks use the web and network traffic as a primary threat vector to compromise key systems, perform reconnaissance on network security, establish long-term control and access, and steal data.
FireEye Network Security (NX) products, now available in modular 2- and 4-Gbps appliances, enable organizations to prevent, detect, and respond to zero -day exploit attempts against network security. It also defends networks from web drive-by downloads, and advanced malware that routinely bypasses conventional signature-reliant defenses. The add-on Secure Sockets Layer (SSL) Intercept appliance gives Network Security products visibility into SSL traffic to detect and block encrypted attacks.
Some of the Benefits of Network Security:
- Prevent network-based cyber attacks
- Detect advanced malware that compromises network security
- Respond faster to threats against network security
Some of the Features of Network Security:
- Real-time threat prevention blocks web-based attacks
- Protects against unknown, zero-day attacks
- YARA-based rules enable customization
- Streamlined incident prioritization
- Dynamic threat intelligence sharing
- Fights blended attacks across web and email threat vectors
- No tuning and near-zero false positives
- Active fail open support
- IPS support
Learn more about FireEye Network Security Products (download the Product Datasheet)
Cyber criminals often use spear phishing attacks, as well as malicious file attachments and URLs in emails, to launch an advanced cyber attack. These email attacks routinely bypass email security that uses conventional signature-based defenses such as antivirus (AV) and antispam filters (AS).
FireEye Email Security products (EX and ETP) protect against such cyber attacks. These products detonate and analyze suspicious email attachments and embedded URLs and block malicious activity to enhance email security. With these capabilities, organizations can prevent, detect, and respond to email-based cyber attacks. AV and anti-spam protection are available to handle casual attacks and nuisance traffic. And customers can select Email Threat Prevention Cloud (ETP) for a complete, off-premise email security solution with no hardware or software to install.
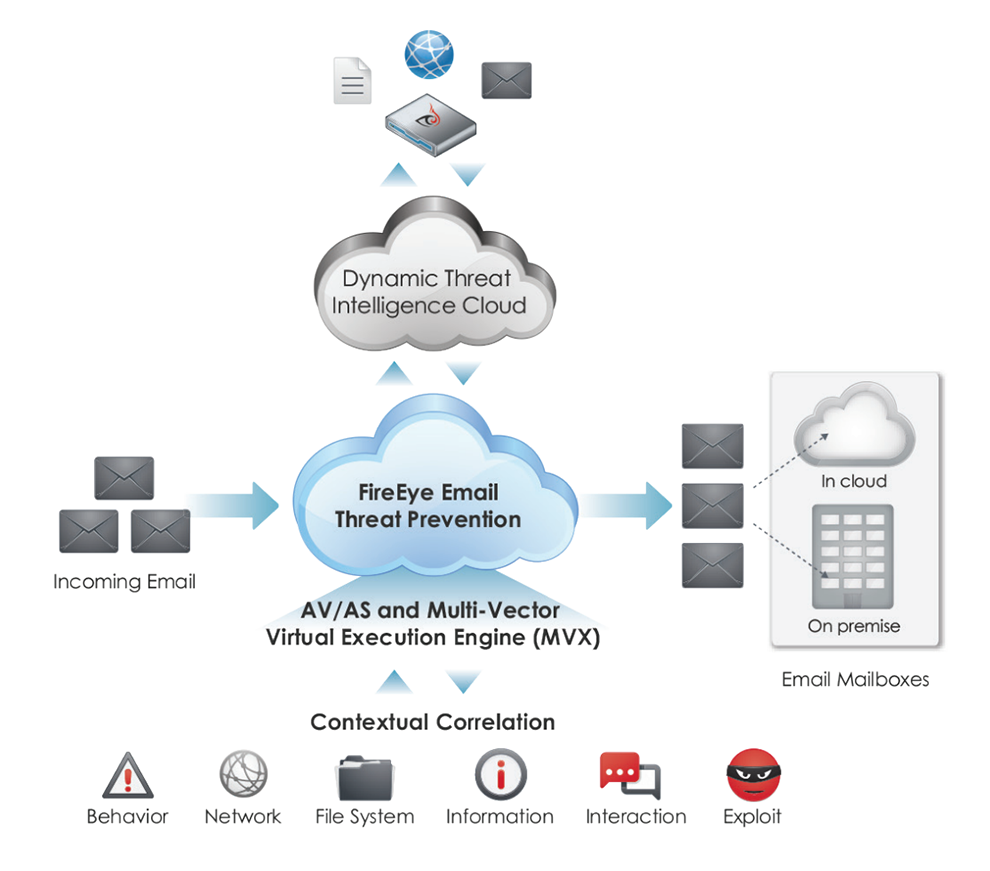
Some of the Benefits of Email Security:
- Get complete protection against email-based cyber attacks
- Detect unknown malware and malicious links with the industry's most advanced intelligence
- Respond to incidents faster
Some of the Features of Email Security On Premise (EX Series):
- Easy deployment and cross-enterprise protection
- Operational effectiveness
- Deploy in active protection-mode or monitor only
- Real-time quarantine of malicious emails
- Multi-vector virtual execution in the cloud
- Security across email and web threat vectors
- Easy-to-use management portal
Some of the Features of Email Security in the Cloud (ETP):
- Real-time quaratine of malicious emails
- Threat intelligence sharing across the enterprise
- Streamlined email threat management
- YARA-based rules enables customization
- Comprehensive email security
- Dynamic analysis of zero-day email attacks
- Fights blended attacks across Web and email threat vectors
Learn more about Email Security On Premise (EX Series) (download the Product Datasheet)
Learn more about Email Security in the Cloud (ETP) (download the Product Datasheet)
File content security, which would cover online file shares, portable file storage and services such as SharePoint, is a significant concern for your networks. Advanced cyber attackers can breach file content security and then launch advanced attacks capable of compromising key systems in an organization.
FireEye File Content Security (FX Series) products help prevent, detect and respond to cyber attacks by scanning file content for signs of malicious threats. These threats might be brought into an organization from outside sources, such as online file sharing services and portable file storage devices.
Some of the Benefits of File Content Security:
- Prevent file share-based cyber attacks
- Detect advanced malware
- Respond to incidents faster
Some of the Features of File Content Security:
- Finds latent malware undetected by traditional AV software engines
- Can deploy in active quarantine (protection mode) or analysis only (monitor mode)
- Executes recursive, scheduled and on-demand scans of Common Internet File System (CIFS)- and Network File System (NFS)-compatible file shares
- Provides proactive SharePoint protection by leveraging Web Distributed Authoring and Versioning (WebDAV) protocol
- Includes analysis of a wide range of file types, including PDFs, Microsoft Office documents and multimedia files
- Integrates with the FireEye AV-Suite to streamline incident response prioritization and naming conventions
- Shares threat data with FireEye platforms through the FireEye Central Management (CM) and FireEye Dynamic Threat Intelligence (DTI) cloud
Learn more about FireEye File Content Security (download the Product Datasheet)
To reduce the impact of a security incident, organizations should focus on early detection and swift investigation. Enterprise forensics makes this possible. When attacked, an enterprise needs to be able to rapidly investigate and determine the scope and impact of the incident so they can effectively contain the threat and re-secure their network.
The FireEye Network Forensics Platform (PX series) and the Investigation Analysis system (IA series) are a powerful combination, pairing the industry's fastest lossless network data capture and retrieval solution with centralized analysis and visualization. Enterprise forensics combines high performance packet capture with analysis tools to aid investigation efforts. It complements several other FireEye threat prevention and detection capabilities.
Some of the Benefits of Enterprise Forensics:
- Investigate and respond immediately
- Analyze attacker tactics and assess impact
- Centralized visibility across the network
Some of the Features of Network Forensics Platform (PX series):
- Continuous, lossless packet capture with nanosecond time stamping at recording speeds up to 20 Gbps
- Real-time indexing of all captured packets using time stamp and connection attributes and export of flow index in NetFlow versions 5 and 9 and Internet Protocol Flow Information Export (IPFIX) for use with other flow analysis tools
- Ultrafast search and retrieval of target connections and packets using patent-pending indexing architecture
- Web-based, drill-down GUI for search and inspection of packets, connections and sessions
- Session decoder support for viewing and searching web, email, FTP, DNS, chat, SSL connection details and file attachments
- Packet payload search using regular expressions
- Industry-standard data storage and export in packet-capture (PCAP) format, which can be stored with flexible storage options: on the appliance, SAS-attached or SAN-attached
- Acceleration of the investigative process via event-based capture to identify suspicious sessions that should be the focus for deeper investigations
Some of the Features of Investigation Analysis system (IA series):
- Visualization: view and share network metadata and activity through easy-to-create custom dashboards
- Fast Answers: centralized application-level wildcard queries and investigation across packet-capture nodes
- System Information and Event Management (SIEM) integration: via representational state transfer (REST) API access to flow and metadata indices
- Workflow Efficiency: archive and share packet-capture (PCAP) files with other analysts during an investigation through integrated case management
- Powerful Search: index metadata from protocols such as HTTP, SMTP, POP3, IMAP, SSL, TLS and FTP
Learn more about Network Forensics Platform (PX series) (download the Product Datasheet)
Learn more about Investigation Analysis system (IA series) (download the Product Datasheet)
Most deployed endpoint systems use traditional security that relies on signature-based defenses. Skilled attackers can readily bypass these defenses. Organizations need to address this security gap. FireEye now offers its industry-leading threat detection capabilities from the network core to the endpoint with FireEye Endpoint Security (HX Series). With this solution, you can enhance endpoint visibility and enable a flexible and adaptive defense against known and unknown threats.
Endpoint Security automatically updates your endpoints with available threat intelligence and inspects them to see if there is a corresponding threat or indicator of compromise (IOC) when FireEye detects an attack anywhere in a network. Compromised endpoints can be isolated with a single click while security teams use the Enterprise Security Search feature to identify known or unknown threats on other endpoints. Security teams can also use the Data Acquisition feature, which allows analysts to inspect compromised endpoints and analyze gathered information to create custom IOCs and address previously unknown threats. As a result, security teams gain deeper insights into attacker behavior and tools via detailed information on the vulnerabilities and risks of your on- and off-premise endpoints.
Some of the Benefits of Endpoint Security:
- Improved threat detection and visibility
- Enhanced validation and immediate containment
- Fast Enterprise Search Functionality
- Smarter analysis and faster incident response
Some of the Features of Endpoint Security:
- Extend integrated FireEye Threat Intelligence from core to endpoint for comprehensive protection against advanced threats
- Conduct detailed endpoint investigations to identify and contain IOCs and create event timelines with Triage Viewer
- Detect, identify and contain threats on tens of thousands of endpoints (connected or not) in minutes via Enterprise Security Search
- Respond rapidly to known and unknown threats with critical contextual information
- Protect all endpoints whether on- or off-premise, outside the network, or behind network address translation (NAT)
- Contain threats and compromised devices with a single click while still allowing for remote investigation
Learn more about FireEye Endpoint Security Products (download the Product Datasheet)
Malware analysis is an important part of preventing and detecting future cyber attacks. Using malware analysis tools, cyber security experts can analyze the attack lifecycle and glean important forensic details to enhance their threat intelligence.
Malware Analysis (AX series) products provide a secure environment to test, replay, characterize, and document advanced malicious activities. Malware Analysis shows the cyber attack lifecycle, from the initial exploit and malware execution path to callback destinations and follow-on binary download attempts.
Some of the Benefits of Malware Analysis:
- Gain insight into cyber attacks to lower business risk
- Automated analysis to improve efficiency
- Single-test environment for Windows and MacOS
Some of the Features of Malware Analysis (AX series):
- Performs deep forensic analysis through the full attack life cycle, using the FireEye MVX engine
- Streamlines and batches analysis of suspicious web code, executables and files
- Reports in-depth on system-level OS and application changes to file systems, memory and registries
- Offers live-mode or sandbox analysis to confirm zero-day exploits
- Dynamically generates threat intelligence for immediate local protection via integration with the FireEye Central Management (CM) platform
- Captures packets to allow analysis of malicious URL sessions and code executions
- Includes the FireEye AV-Suite to streamline incident response prioritization
- Includes support for Windows and Mac OS X environments
Learn more about Malware Analysis (AX series) (download the Product Datasheet)
With every new layer of cyber security you put in place, the attackers respond by evolving their own tools and techniques. To combat this constantly changing threat you, too, need a new approach: FireEye as a Service.
This is not your usual managed security service or your typical managed security services provider (MSSP) arrangement. With FireEye as a Service, our threat analysts are an extension of your cyber security team. The analysts provide:
- Insight and intelligence from the front lines of incident responses
- Proactive hunting for indicators of compromise (IOCs) in your environment
- Around-the-clock monitoring for indications that a cyber attack has bypassed your technology defenses
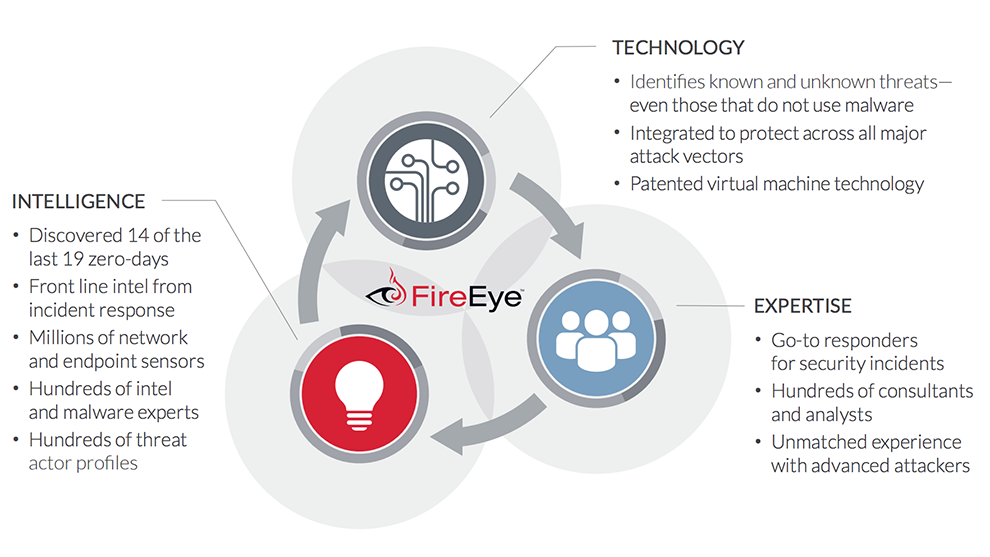
Having swift detection, analysis, and response means attackers never gain a foothold and your business assets stay safe.
Some of the Benefits of FireEye as a Service:
- Continuous monitoring by experts
- Answers, not alerts
- Reduce the consequences of a breach
Some of the Features of FireEye as a Service:
- Monitoring by Experts: patented FireEye technology augmented by expert security analysts monitoring 24x7 reduces average threat detection and response time from months to minutes
- Applied Intelligence: mobilizes the latest tactical intelligence to find threats in your environment faster by operationalizing information flow from front-line incident responders, network virtual machines (VMs) and endpoint sensors across the FireEye global defense community
- Answers, Not Just Alerts: validated compromise reports contain information about attackers and their intentions, and then tell you how to respond
- Purchasing Choice: flexible subscription and capital expense options allow you to match your security needs with payment preferences
- Managed security service provider (MSSP)-Friendly: complements and strengthens the services of your existing managed security partner
Learn more about FireEye as a Service (download the Product Datasheet)
